When people talk about WebRTC security, the conversation usually jumps straight to encryption. DTLS-SRTP, secure signaling, HTTPS everywhere — all important, all necessary. But there is another class of risk that quietly causes just as many real-world problems, and it is far less discussed: IP address exposure.
In WebRTC systems, IP addresses are not just technical details. They reveal topology, infrastructure placement, internal network design, and sometimes even user location. Leak the wrong IPs in the wrong place, and you are effectively giving attackers a map of where to aim next.
This article focuses entirely on IP address security in WebRTC environments, how leaks happen, why they matter, and how proxy-based designs — including how Siperb operates — dramatically reduce the attack surface.
Why WebRTC is naturally “chatty” about networks
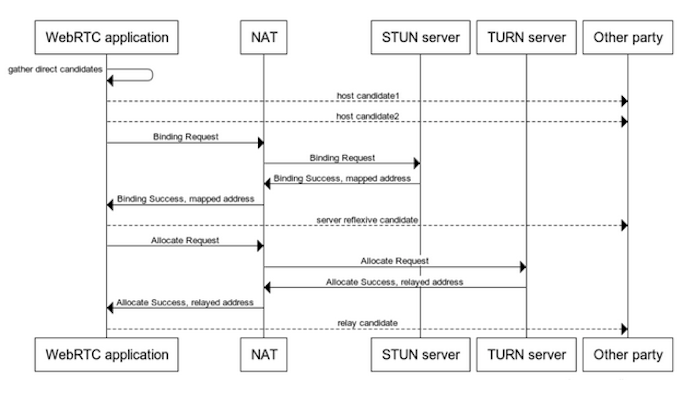
WebRTC was designed to make real-time media work reliably across wildly different networks. Home Wi-Fi, corporate NATs, mobile carriers, coffee shops — all of them behave differently. To handle this, WebRTC relies on ICE (Interactive Connectivity Establishment), which actively discovers possible network paths between endpoints.
That discovery process involves exchanging candidates, which are essentially network coordinates: IP addresses and ports that might work for media. Depending on configuration, those candidates can include:
- private/local IP addresses
- public IP addresses
- relay addresses from TURN servers
From a connectivity perspective, this is brilliant. From a security and privacy perspective, it means WebRTC is constantly sharing network information unless you deliberately design around it.
Why IP addresses are valuable intelligence
An IP address on its own might seem harmless. After all, everything on the internet has one. The problem is not that an IP exists, but what it represents.
In real deployments, leaked IP addresses can tell an attacker:
- where your PBX or SBC is hosted (cloud provider, region, pattern)
- whether infrastructure is centralized or distributed
- which ports are open and responding
- whether internal/private addressing is leaking through NAT
- how traffic flows between components
This kind of information dramatically lowers the cost of attack. Instead of scanning blindly, attackers can focus on known targets with known behavior. SIP scanners, brute-force tools, and targeted DoS attacks all become more effective once the topology is partially exposed.
Just as importantly, IP leaks are often silent. Nothing breaks. Calls still work. Users don’t complain. Meanwhile, your infrastructure becomes increasingly visible to anyone who knows where to look.
The hidden danger of direct PBX exposure
One of the most common WebRTC architectures is also one of the riskiest: browsers registering directly to a PBX over the public internet.
In this model, the PBX must be reachable from anywhere the user might be. That almost always means:
- a public IP or exposed port
- permissive firewall rules
- NAT traversal rules that are hard to reason about
- SIP responses that reveal software behavior and headers
Even if authentication is strong, exposure alone invites attention. SIP servers are constantly scanned. Automated tools don’t care whether you are “small” or “not a target.” If your PBX responds, it gets indexed.
Once attackers know where the PBX lives, they can apply pressure in many ways: registration floods, malformed packets, brute-force attempts, or simple traffic exhaustion. At that point, security becomes a race between defensive tuning and attacker persistence.
How topology leaks happen (even when you think they don’t)
IP address exposure in WebRTC is rarely a single mistake. It is usually the result of small, reasonable decisions adding up.
SIP signaling can include internal IPs in headers if topology hiding is not enabled. SDP bodies can reveal media endpoints that point deeper into the network than intended. ICE candidates may expose private interface details if not filtered correctly. Debug logging and diagnostics can accidentally surface real addresses in client-facing tools.
None of these issues are catastrophic in isolation. Together, they form a surprisingly clear picture of how your system is built.
This is why IP security should be treated as a design concern, not a patch applied after deployment.
Why hiding topology is not about secrecy — it’s about boundaries
Topology hiding is sometimes misunderstood as “security through obscurity.” In reality, it is about enforcing clean boundaries between trust zones.
Your internal network has no reason to be visible to browsers. Your PBX does not need to reveal where it lives to every endpoint. Your media paths do not need to expose internal routing decisions to the outside world.
When a system presents a single, controlled edge to the internet, you gain leverage. You can monitor, rate-limit, filter, and adapt without constantly exposing the components behind it. This is not about pretending attackers don’t exist — it’s about limiting what they can see and touch.
How Siperb uses a proxy to reduce IP exposure
This is where a proxy-based WebRTC architecture fundamentally changes the security equation.
With Siperb, WebRTC clients do not need to know where the PBX lives. They interact with a controlled edge instead. That edge terminates signaling, manages media routing, and presents a consistent external surface regardless of how complex the internal system becomes.
By doing this, Siperb can provide topology hiding as a natural outcome of the architecture. Internal IP addresses stay internal. PBX locations are not advertised to browsers. SIP headers and SDP can be normalized and sanitized before they ever reach the client.
From the outside, there is far less to enumerate. From the inside, infrastructure can evolve without changing what clients see. This separation is valuable not only for security, but also for operational flexibility and scale.
IP security also protects user privacy
There is another angle that is often overlooked: user IP privacy.
In peer-to-peer WebRTC calls, users can potentially learn each other’s public IP addresses. In consumer scenarios, this can be a privacy concern. In business environments, it can expose internal corporate networks or employee locations.
By anchoring media through relays and proxies when appropriate, you can prevent unnecessary disclosure of user IPs. This is not always required, but when privacy matters, having the option is critical.
Again, this is easier to achieve when clients connect to an intermediary rather than directly to each other or directly to core infrastructure.
Designing WebRTC systems with IP exposure in mind
Good IP security does not mean “hide everything at all costs.” It means being intentional about what is exposed and why.
A well-designed WebRTC system typically ensures that:
- PBXs and internal services are not directly reachable from the public internet
- clients terminate on a controlled edge
- internal IPs do not leak through SIP headers or SDP
- media paths are predictable and inspectable
- external observers see only what they need to see
When these principles are applied early, security improves almost as a side effect. When they are applied late, they become difficult and disruptive retrofits.
In WebRTC, IP addresses tell stories. They reveal how your system is built, where it lives, and how it might be attacked. Most leaks are not dramatic, but they are cumulative, and attackers are patient.
By treating IP address exposure as a first-class security concern, and by using proxy-based designs that enforce clean boundaries — like the approach taken by Siperb — you reduce both risk and complexity. Your infrastructure becomes harder to map, harder to target, and easier to protect.
Strong WebRTC security is not just about encrypting packets. It is about controlling visibility. And when it comes to IP addresses, less visibility almost always means more security.

Leave a Reply